Enhancing Election Integrity Through Data-driven Poll Worker Training
Free and fair elections and voting integrity are fundamental components of healthy democracies. In the U.S., poll workers play a critical role by administering elections and ensuring their legitimacy. However, recent public discourse has raised concerns about potential security risks that stem from poll workers, who may make honest mistakes or perhaps even act with malicious intentions during an election. In light of these concerns, the Empowering Secure Elections (ESE) Research Lab at Towson University examines poll workers, mail-in ballots, and electoral processes in the U.S. to identify sources of risk, calculate relative risk, develop attack trees, and provide recommendations that will ensure the integrity of votes from cast to count [1, 4-8].
Election equipment is critical infrastructure in the U.S., and the highly seasonal (and often volunteer) poll workers have access to all of the necessary apparatuses to effectively oversee election processes at polling places. The use of analytics—such as foundational artificial intelligence (AI) and data mining—can address poll workers’ specific needs and help to maintain the security and integrity of voting protocols. By understanding the unique backgrounds of different poll worker groups, election administrators can develop targeted training programs and implement proactive measures that mitigate insider risks, optimize resources, and enhance the effectiveness of efforts to safeguard election integrity.
The Security Behavior Intentions Scale (SeBIS) is a 16-question survey that assesses individuals’ self-reported intentions to follow common security practices on four factors: (i) Device securement, (ii) password generation, (iii) proactive awareness, and (iv) updating [3]. SeBIS—which has been validated by the usable security community—measures intent (not actual behavior) to inquire about respondents’ interactions with computer equipment and devices [2]. Ongoing work in the ESE Research Lab utilizes SeBIS in a variety of contexts, including the anonymous collection of inventory responses from 2,213 U.S. poll workers [9]. The data involves five-point Likert scale responses that range from strongly disagree to strongly agree for all SeBIS inventory questions, along with demographic information such as age, education level, poll worker location, and familiarity with computers. Figure 1 displays the SeBIS questions and the mean, median, and standard deviation of the responses. We inverted the response scale for analysis for questions F5, F8, F9, F10, F11, and F13 in the SeBIS inventory, as the original wording was negative.
![<strong>Figure 1.</strong> Security Behavior Intentions Scale (SeBIS) inventory questions and the mean, median, and standard deviation of the responses from a survey of 2,213 U.S. poll workers. Figure adapted from [7, 9].](/media/3jypzgs2/figure1.jpg)
Cluster analysis is a form of unsupervised learning that groups all objects or data together that are similar (or related) to one another and different from (or unrelated to) those in other groups; specifically, it maximizes inter-cluster distances and minimizes intra-cluster distances. More broadly, unsupervised learning is a form of machine learning that uses foundational AI to identify patterns, structures, or relationships within data — especially ones that are not immediately apparent via manual analysis. The application of unsupervised learning to SeBIS poll worker data creates clusters that offer valuable insights into the characteristics and behaviors of poll workers, which can then inform targeted interventions and policy decisions that are based on the needs and challenges of each cluster.
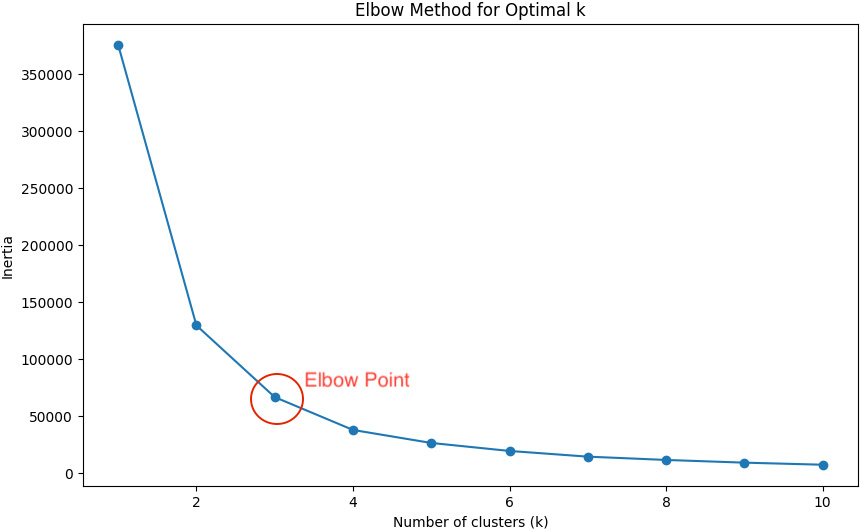
One specific cluster analysis algorithm, called \(k\)-means, partitions the dataset into \(k\) distinct, non-overlapping clusters wherein each data point belongs to the cluster with the nearest mean (or centroid). We employed the standard elbow method to determine the optimal \(k\) by plotting the within-cluster sum of squares against the number of clusters; the rate of decrease sharply levels off at the elbow point, which indicates the optimal number of clusters for the dataset in question. Figure 2 suggests that \(k=3\) clusters is best for our poll worker data.
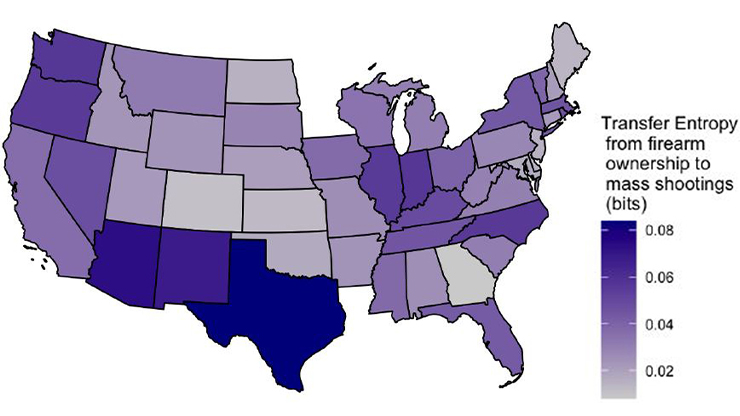
Each cluster represents a unique profile of poll workers that is based on their demographic and SeBIS inventory responses. Following this segmentation, we examined disparities between patterns within the clusters (see Figure 3). Specifically, cluster 1 \((n_1=425)\) comprises the youngest participants (mode \(=\) 35 to 44 years old), whereas clusters 2 \((n_2=1131)\) and 3 \((n_3=657)\) generally consist of older individuals (mode \(=\) 65 to 74 years old). Education levels are similar across all clusters, and the mode for every column is a bachelor’s degree. Clusters 2 and 3 exhibit a slightly higher amount of poll working experience (mode \(=\) more than 3 years) when compared to cluster 1 (mode \(=\) 0 to 1 years). Additionally, participants in clusters 1 and 2 report a lower level of familiarity with computers (mode \(=\) not comfortable) than those in cluster 3 (mode \(=\) somewhat comfortable). Cluster 2 generally reveals the highest security behavior intentions across all SeBIS inventory questions \((\mu=4.18)\) — a promising result for election security, as this cluster contains the largest group of poll workers (about half of the surveyed population). Cluster 1 has moderately high security intentions \((\mu=3.77)\), while cluster 3’s reported intentions are lower \((\mu=3.31)\). Figure 3 illustrates the average Likert response by cluster.
Training programs must be tailored to accommodate the varying levels of familiarity and expertise among poll workers, especially given the differing ages and experience levels among the clusters. Moreover, the varying but considerably poor level of computer familiarity across clusters presents an opportunity to enhance efficiency and integrity in the electoral process by incorporating additional technology training into poll worker education programs. A heightened emphasis on communication and collaboration skills can foster effective interactions between voters and poll workers, leading to smoother operations on Election Day and stronger public trust in the electoral process.
We recommend targeted training programs for cluster 3 to support individuals’ expertise and enhance their effectiveness as poll workers. Leadership and team development initiatives may compel more experienced poll workers to assume mentorship roles to support and guide their colleagues. For poll workers in clusters 1 and 2, targeted training can increase comfort with electronic voting equipment and ensure effective participation. Furthermore, tailored support and additional resources for those who struggle with technology can help avoid honest mistakes with election equipment. Such training could focus on basic computer skills and involve on-site assistance from experienced poll workers and technical support staff.
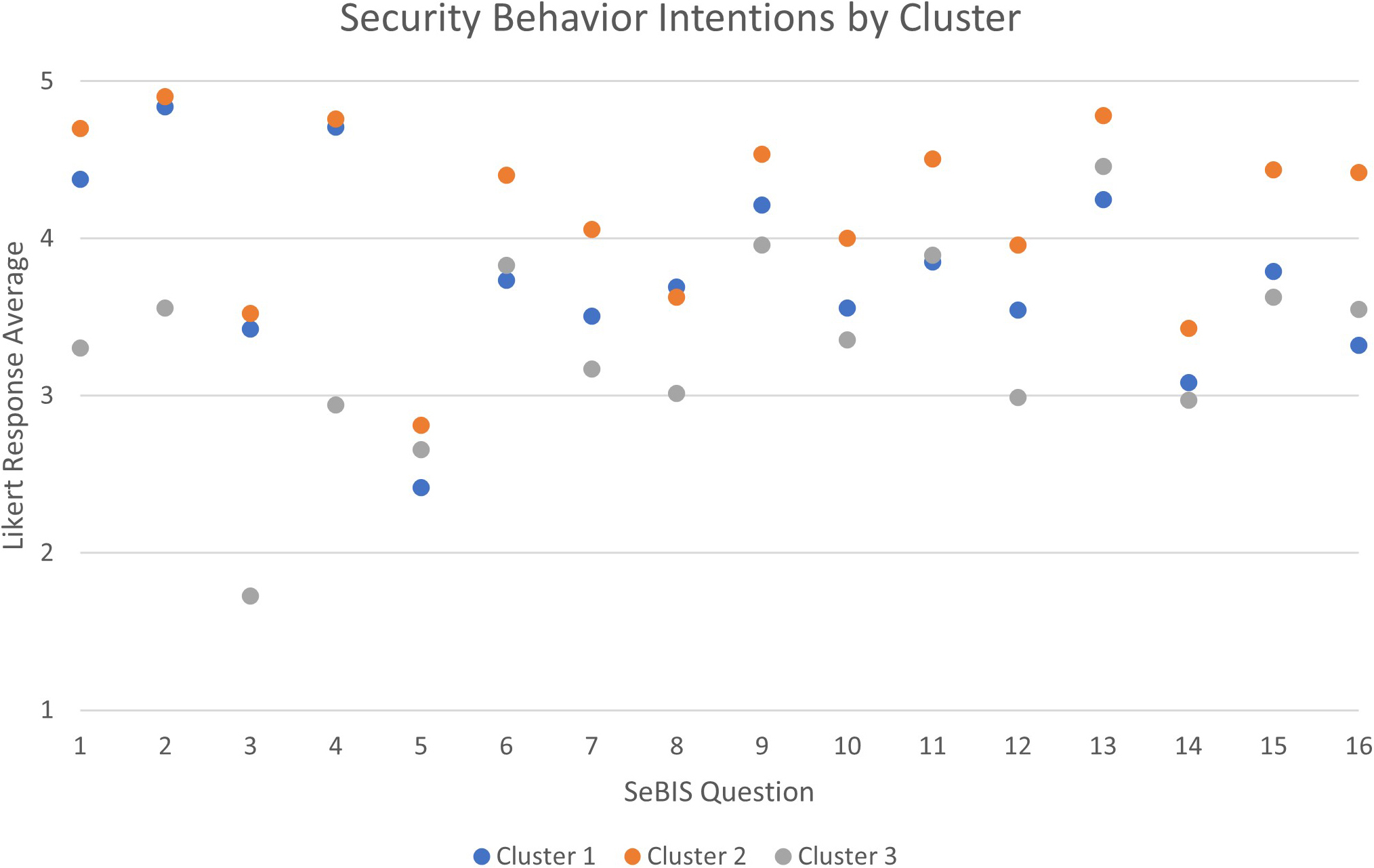
By analyzing the specific SeBIS security behavior intentions with lower scores in cluster 3, election administrators can target areas for improvement and implement interventions that address gaps in knowledge or skills — thereby promoting continuous improvements in security and ensuring a smoother voting experience at polling stations. Interestingly, however, poll workers who indicate some comfort with computers exhibit poorer security behavior intentions than those who are less familiar with technology; perhaps increased comfort leads to lax security behaviors.
Ultimately, higher SeBIS scores imply positive security behavior intentions (note that SeBIS does not measure actual behavior and is instead predictive because it queries future intent). However, insight into poll workers’ perceptions of technology and interactions with critical election equipment can inform election officials about potential risks from honest mistakes or misuse. Given the connection between intent and potential behaviors, it is important to understand that useful security knowledge can influence or alter both factors. Poll workers can learn about threats by completing online training [6]. Because these workers assume significant responsibilities throughout the election process, the mitigation of insider risks supports the integrity of elections and polling places. Although the prediction of specific threats is extremely challenging, training can curtail opportunities for both unintentional and adversarial insider events. In the U.S., all registered voters can serve as poll workers, and no one should be denied that privilege. As such, targeted training can help to bridge knowledge gaps and build a secure and trusted poll worker staff for Election Day.
Acknowledgments: The authors thank Vincent Schiavone for his feedback on this article; Sandra Dehlinger, Michele Scala, and Michael Scala for assisting with data collection; and the thousands of anonymous poll workers who responded to the survey.
References
[1] Dehlinger, J., Harrison, S., & Scala, N.M. (2021). Poll worker security: Assessment and design of usability and performance. In Proceedings of the 2021 IISE annual conference (pp. 698-703). Institute of Industrial and Systems Engineers.
[2] Egelman, S., Harbach, M., & Peer, E. (2016). Behavior ever follows intention? A validation of the Security Behavior Intentions Scale (SeBIS). In CHI ’16: Proceedings of the 2016 CHI conference on human factors in computing systems (pp. 5257-5261). San Jose, CA: Association for Computing Machinery.
[3] Egelman, S., & Peer, E. (2015). Scaling the security wall: Developing a security behavior intentions scale (SeBIS). In CHI ’15: Proceedings of the 33rd annual ACM conference on human factors in computing systems (pp. 2873-2882). Seoul, South Korea: Association for Computing Machinery.
[4] Kassel, A., Bloomquist, I., Scala, N.M., & Dehlinger, J. (2024). Understanding the impact of poll worker cybersecurity behaviors on U.S. election integrity. In Proceedings of the IISE annual conference and expo 2024. Montreal, Canada: Institute of Industrial and Systems Engineers.
[5] Locraft, H., Gajendiran, P., Price, M., Scala, N.M., & Goethals, P.L. (2019). Sources of risk in elections security. In Proceedings of the 2019 IISE annual conference (pp. 1572-1577). Orlando, FL: Institute of Industrial and Systems Engineers.
[6] Scala, N.M., Dehlinger, J., & Black, L. (2023). Preparing poll workers to secure U.S. elections. In Proceedings of the American Society for Engineering Management 2023 international annual conference (pp. 1-11). Denver, CO: American Society for Engineering Management.
[7] Scala, N.M., Dehlinger, J., & Mezgebe, Y. (2022). Securing organizations from within: Opportunities and challenges of trusted insiders. Baltimore Business Review, pp. 16-20.
[8] Scala, N.M., Goethals, P.L., Dehlinger, J., Mezgebe, Y., Jilcha, B., & Bloomquist, I. (2022). Evaluating mail‐based security for electoral processes using attack trees. Risk Anal., 42(10), 2327-2343.
[9] Scala, N.M., Rajgopal, J., Mezgebe, Y., & Dehlinger, J. (2024). An information-theoretic analysis of security behavior intentions amongst United States poll workers. Risk Anal., to appear.
About the Authors
Hao Nguyen
Towson University
Hao Nguyen holds a M.S. in supply chain management from Towson University. She has over six years of experience in the field and specializes in data analysis, with a focus on poll worker education and the information security behavior of professionals in various industries.

Navya Gautam
Master's student, Georgia Institute of Technology
Navya Gautam is a master's student in computer science at the Georgia Institute of Technology. She holds a B.S. in both mathematics and computer science from the University of Maryland.

Shreenidhi Ayinala
Undergraduate student, University of Maryland
Shreenidhi Ayinala is a junior at the University of Maryland, where she is majoring in both computer science and mathematics with a minor in computational finance. Her interests lie in machine learning and data science, particularly at the intersection of computer science and mathematics.

Natalie M. Scala
Professor, Towson University
Natalie M. Scala is a professor in the College of Business and Economics, a fellow of the Center for Interdisciplinary and Innovative Cybersecurity, and director of accelerated programs at Towson University. Her primary research lies in decision analysis with a specialization in military and security issues, including risk in voting systems, attack trees and strength of threat in mail voting, integrity of votes throughout the supply chain, poll worker education, and cybersecurity metrics and best practices.

Josh Dehlinger
Professor, Towson University
Josh Dehlinger is a professor in the Department of Computer and Information Sciences at Towson University. His research expertise lies in software safety and reliability, election security, machine learning for software engineering, and computer science education.

Stay Up-to-Date with Email Alerts
Sign up for our monthly newsletter and emails about other topics of your choosing.